(SecurityWeek- Eduard Kovacs) – A survey conducted by the Ponemon Institute on behalf of security solutions provider TUV Rheinland OpenSky analyzes the security, safety and privacy challenges and concerns related to the convergence between information technology (IT), operational technology (OT), and industrial internet of things (IIoT).
Industrial systems are increasingly sophisticated and automation plays a critical role in ensuring efficiency, which has led to IT, OT and IIoT systems becoming increasingly integrated. However, there are several challenges and concerns that need to be addressed to achieve convergence.
The study conducted by TUV and Ponemon is based on responses from over 650 individuals from organizations of all sizes, representing sectors such as automotive, oil and gas, energy, healthcare, industrial manufacturing, logistics and transportation, consumer goods and retail, and telecommunications. A vast majority of the companies (99%) have employees in the United States, but many also have employees in Canada (67%), Europe (69%), the APAC region (58%), Latin America (54%), and the Middle East and Africa (35%).
Roughly two-thirds of respondents said they believe IT and OT convergence is a good thing and that it’s being driven by digitalization. Over 60% of respondents believe convergence is important for achieving a more mature security posture, and nearly half believe it’s an important factor for improving the trust and confidence of supply chain partners.
However, according to the study, many believe convergence cannot be achieved without support from the company’s chief information officer (CIO) and other C-level executives. At least half of respondents also said convergence is not possible without strict safeguards for critical operations data, and it’s not possible if the organization has a long history of silos and turf issues.
“Conflicts created by turf and silo issues are a significant organizational barrier to successful convergence. The creation of a cross-functional team to manage cyber risk across IT and OT systems will help eliminate this problem,” the report says.
At least half of respondents claimed their organization is highly effective in achieving various tasks that are crucial for convergence, including safety program management, cybersecurity planning, leadership and governance, security program management, awareness and training, incident preparedness, testing and assessment, and threat and risk analysis. Fewer companies claim to be good in areas such as third-party risk management, compliance with regulations and standards, and privacy program management.
Respondents said they believe resilience, agility, a strong security posture, and expert staff are the most critical factors for ensuring a successful convergence process.
This process is in many cases managed through a combination of in-house and outsourced expertise (46%), followed by only in-house teams (34%), and only external service providers (20%).
When it comes to budgets allocated for convergence, 45% of respondents said they have a budget, but 50% said they do not have a budget for it.
The inability to overcome turf and silo issues has been cited by more than half of respondents as a barrier to the successful convergence of cybersecurity, functional safety and data privacy. Other barriers cited by a significant number of respondents include the inability to control security, safety and privacy initiatives, the inability to secure assets and infrastructure, the inability to ensure the free flow of information, and the lack of in-house expertise.
The lack of skilled employees is considered the most common problem for a strong convergence process, along with insufficient risk assessment.
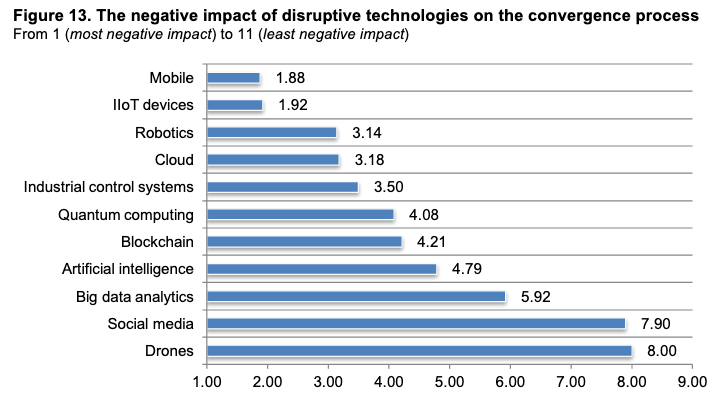
Many organizations believe that mobile and IIoT devices have the most negative impact on convergence.
The study found that while safety objectives are in many cases at least partially aligned with business objectives, privacy objectives and cybersecurity objectives are less likely to be aligned. On the other hand, over 70% said cybersecurity is the most influential to their company’s business strategy, while privacy is the least influential.
While security is considered important during the convergence process, many organizations don’t appear to be able to maintain a strong cybersecurity posture, but they are more confident in their ability to maintain a strong safety posture.
The complete report, “Safety, Security & Privacy in the Interconnected World of IT,OT& IIoT,” is available for download in PDF format.
Study Analyzes the Challenges and Concerns for IT/OT Convergence
(SecurityWeek- Eduard Kovacs) - A survey conducted by the Ponemon Institute on behalf of security solutions provider TUV Rheinland OpenSky analyzes the security, safety and privacy challenges and concerns related to the convergence between information technology (IT), operational technology (OT), and industrial internet of things (IIoT). Industrial systems are increasingly sophisticated and automation plays a critical role in ensuring efficiency, which has led to IT, OT and IIoT systems becoming increasingly integrated. However, there are several challenges and concerns that need
Critical Flaws Allow Hackers to Take Control of Kunbus Industrial Gateway
(SecurityWeek - Eduard Kovacs) - Several serious vulnerabilities have been identified in a gateway made by Kunbus, including flaws that can be exploited to take complete control of a device. Germany-based Kunbus offers connectivity solutions for industrial networks. The company’s gateway products, which are used by various types of organizations around the world, are designed to provide continuous and reliable communications between different networks and systems. Kunbus Industrial Gateway Nicolas Merle, a researcher with industrial cybersecurity firm Applied Risk, discovered that Kunbus’ PR100088
ICS Red Team/Blue Team Training (Singapore)
SecurityWeek is pleased to offer the following optional workshop for attendees of our 2019 Singapore ICS Cyber Security Conference, taking place April 16-18, 2019. When: Thursday, April 18, 2019 – 8AM-5PM ($400 Fee – Limited to 40 Students – Register Now) What is red team/blue team training? Security aware and knowledgeable users serve as the “front line” of your overall security posture. As such, training is one of the most essential components of your risk mitigation strategy and overall cybersecurity program. However, without learning cybersecurity from the “hacker’s”
Russia, China Can Disrupt Critical Infrastructure: U.S. Intelligence Report
(Eduard Kovacs - SecurityWeek) - Russia and China are capable of disrupting critical infrastructure in the United States, and Iran is not far behind, according to the Worldwide Threat Assessment made public by the U.S. intelligence community on Tuesday. The assessment covers a wide range of threats, including cyber. Similar to the reports published in the past years, it warns that the US’s adversaries and competitors will increasingly use their cyber capabilities for political, military and economic advantage. China and Russia continue
New Training: Advanced ICS/IIoT Security 1-Day Training (Singapore)
SecurityWeek is pleased to offer the following optional workshop for attendees of our 2019 Singapore ICS Cyber Security Conference, taking place April 16-18, 2019. When: Thursday, April 18, 2019 - 8AM-5PM ($400 Fee - Limited to 40 Students - Register Now) Industrial Control Systems (including DCS, HMI, PLC, SCADA, SIS) and Industrial IoT are often poorly understood, yet they are used in the most critical environments in the world. Although they generally remain unseen they are responsible for the smooth running of our
Leadership, Security, and Support at the Clinton White House
Presented at SecurityWeek's 2018 ICS Cyber Security Conference How would you handle leadership in this the most stressful Chief Information Officer (CIO) job in the World – being the CIO at The White House? Colonel Gelhardt answers this question, and talks about the leadership and mentorship he used and how you can use the same skills in the civilian world. If he can do it so can you! Speaker: Colonel Mark Gelhardt - Former CIO for President Clinton
Side-Channel Attacks Put Critical Infrastructure at Risk
ICS Devices Vulnerable to Side-Channel Attacks: Researcher Shows (Eduard Kovacs - SecurityWeek) Side-channel attacks can pose a serious threat to industrial control systems (ICS), a researcher warned last month at SecurityWeek’s ICS Cyber Security Conference in Atlanta, GA. Demos Andreou, a lead engineer at power management company Eaton, has conducted an analysis of protection devices typically used in the energy sector, specifically in power distribution stations. Side-channel attacks can be used to extract data from a system based on information gained by observing
[Video] Hunting for Xenotime, Creators of TRITON-TRISIS ICS Malware
Presented at SecurityWeek's 2018 ICS Cyber Security Conference Speakers: Robert Lee - CEO, Dragos Marc Seitz - Threat Analyst, Dragos The activity group responsible for the TRISIS/TRITON malware is identified as XENOTIME. After the attack on the safety instrumented system in 2017 the group remained active targeting other environments with different safety systems in other regions of the world. Hunting for the behaviors of this group allows defenders to not only search for existing threats but also identify new threats leveraging such
New ISA/IEC Standard Specifies Cybersecurity Capabilities for Control System Components
Research Triangle Park, NC (25 September 2018) – The ISA/IEC 62443 series of standards, developed by the ISA99 committee as American National Standards and adopted globally by the International Electrotechnical Commission (IEC), is designed to provide a flexible framework to address and mitigate current and future security vulnerabilities in industrial automation and control systems (IACS). A newly published standard in the series, ISA/IEC 62443-4-2-2018, Security for Industrial Automation and Control Systems: Technical Security Requirements for IACS Components, provides the cybersecurity technical
Legitimate Remote Admin Tools Pose Serious Risk to Industrial Systems
(SecurityWeek - Eduard Kovacs) - Remote administration tools (RATs) installed for legitimate purposes in operational technology (OT) networks can pose a serious security risk, allowing malicious actors to abuse them in attacks aimed at industrial organizations, Kaspersky Lab warns. A report published on Friday by the security firm reveals that, on average, in the first half of 2018, legitimate RATs were found on more than two-thirds of computers used for industrial control systems (ICS). The highest percentage of ICS computers with RATs



