Guest post by Wojciech [ GitHub Twitter ]
This research is a continuation of the previous one about Industrial Control Systems. This time I will present how Open Source Intelligence can be applied to reconnaissance on critical infrastructure. In many cases it’s possible to narrow a search to specific buildings like power plants, wastewater plants, or chemical and manufactured facilities. The research consists of 26,000 exposed devices in United States.
The research and presentation were prepared for SecurityWeek’s ICS Cyber Security Conference in Atlanta. However, due to visa problems, I’m not able to attend so I’m publishing it as a blog post.

Photo by Matthew Henry on Unsplash
Open Source Intelligence
Open source intelligence (OSINT) is a broad field and it’s used by everyone without even knowing it. What you read or watch impacts your opinion and based on the collected information you believe what you believe in and make your decisions and judgments. Sources of these pieces of information might be traditional mass media — television, radio and newspapers or the Internet and data contained in it — websites, social media, blogs.
Moreover, OSINT is used for different kinds of investigations, from geolocating photos to tracking specific individuals. It is also mixed with other intelligence techniques, like Human Intelligence (HUMINT), Geospatial Intelligence (GEOINT) or of course Cyber Intelligence (CYBINT). Thanks to small leads left in photos or ones left by threat actors, one can gather much information, piece it together, and see the whole image to draw final conclusions.
In addition, OSINT is helpful for cyber crime units to track criminals and for intelligence agencies to gain knowledge about the capabilities of adversaries, in both the real and cyber worlds. Knowing events from Ukraine, Iran and Saudi Arabia, it’s important to be aware of potential damage that may be done to critical country infrastructure. In case of any conflict, devices directly exposed to the Internet might be hacked and damage can be caused in different forms.
The Central Intelligence Agency (CIA) highlights five main OSINT fields:
- The Internet — for this research I used more than information on the Web. I got ICS devices directly connected and exposed to the Internet;
- Traditional mass media;
- Photos — Mostly from social media services and other sources like Google Street View, which was also used in the research;
- Conferences — Where people share their ideas and information; it also includes specialized journals and think tank studies;
- Geospatial information — consists of maps and commercial imagery products. This involves checking geolocation and tracking the nearest building which might be tied to the device;
In this research, however, I used OSINT to visualize and gather geolocation and technical information on about 26,000 exposed ICS devices in United States.

Photo by Wim van ‘t Einde on Unsplash
Critical Infrastructure
It’s hard to clearly determine what is ‘critical infrastructure’ and what is not. In general, it’s sectors and assets that are considered essential for society and national economy, and their destruction or incapacitation would impact national security, healthcare, energy or water sectors. So every building and property responsible for operating in one of 16 sectors, featured by the Department of Homeland Security (DHS), have to be treated as critical infrastructure and should have proper security controls and mechanisms implemented.
To give a better view on it, a parking lot near the shopping center can use Industrial Control System devices, but it won’t be considered critical infrastructure. In contrast to, for example, any power plant — which if hacked and compromised may leave many people and companies without energy — counts as critical infrastructure.
DHS mentions 16 critical infrastructure sectors:
- Chemical — including chemical facilities, pharmaceutical manufacturing or specialty/agricultural chemicals;
- Commercial facilities — places that gather large crowds of people — stadiums, shopping centers, casinos, amusement parks, zoos, or hotels;
- Communication — it provides connectivity across other critical infrastructure and includes wireless, terrestrial and satellite transmissions;
- Transportation — it’s responsible for transporting large amounts of people or goods to different places in a variety of ways. Examples may be railways or airports;
- Manufacturing — involves manufacturing for different industries: primary metals, machinery, electrical equipment and transportation equipment. The manufacturing sector ensures economic prosperity and the continuity of a country;
- Dams — protects from flooding and provides water retention and control services;
- Defense Industrial Base — every facility which manufactures, designs, or delivers military weapons counts as critical infrastructure. Also, industries that provide research and development — government contractors are also in this field. It’s one of the most important sectors in defense as without this it would be impossible to mobilize, deploy and sustain military operations;
- Emergency — this sector is the core of a society’s life. It includes law enforcement and fire departments, public works and medical emergency services. Other services that operate in this sector are SWAT teams, search and rescue teams, fusion centers, canine units, and 911 call centers;
- Energy — provides electricity across cities and businesses. Without a stable energy supply, the rest of the country’s critical infrastructure may be in danger as well. It’s also necessary for day to day activities for everyone;
- Financial — insurance companies, depository institutions and financing organizations;
- Food and Agriculture — it’s highly dependent on the energy, chemical, waste and transportation sectors. Consist of farms, restaurants and food manufacturing;
- Government facilities — all buildings that are state-owned or leased by the state. The most critical facilities in this sector are military installations, national laboratories, courthouses or embassies. Moreover, cyber elements like access-control systems and closed-circuit television systems are included here as well. It also features a subsector for education facilities, which covers schools and institutions of higher education. The election infrastructure responsible for protecting assets like storage facilities and polling places is also a subsector of the government facilities sector;
- Healthcare and Public Health — it protects other sectors from natural/manmade disasters or infectious diseases;
- Information technology — mostly focuses on providing hardware, software and information technology, and together with the communication sector it provides the Internet;
- Nuclear reactors, Materials and Waste — it includes power reactors, research and test reactors or nuclear fuel cycle facilities;
- Water and Wastewater systems — ensure supply of drinking water and wastewater treatment;

OSINT and Critical Infrastructure
Knowing OSINT fundamentals and critical infrastructure sectors we can combine those two things to gather intelligence on a country’s critical assets. Collecting this information is important to understand an adversary’s cyber potential and weaknesses, and it’s done as a first step in every cyber attack.
OSINT for critical infrastructure is mostly used by intelligence services for espionage and potential disruption during warfare or just for showing your own cyber strength. Criminal groups are also interested in compromising the critical sectors of a country, but mostly for monetary gain — they use OSINT for reconnaissance in order to develop and sell malware for ICS or trading stolen credentials. Other groups that may target critical ICS devices and use OSINT are terrorists, whose goal is to weaken the economy, lower public moral and threaten national security. I also count insiders in this group because of their extensive knowledge about already implemented infrastructure. They may not have access to everywhere, but know the network and technology that is used, for example, in power plants.
From open source data we can gather a lot of information about specific buildings of critical infrastructure. It might be geolocation with accuracy to a specific building or city. This allows to gather more info from physical surveillance, social media photos, Google Maps or Street View.
Looking for vulnerabilities or entry points into one of the elements of critical infrastructure, we should not forget about staff working there. Proper reconnaissance allows you to recruit insiders, plant your own spy, but it’s also important for spear phishing.
It’s worth reminding that OSINT is gathering data passively without the target being aware that he is investigated. The door to active reconnaissance opens when you have the technical details of devices, including:
- IP address/hostname — to scan assets nearby or for uncommon ports;
- Technology — allows to find or research vulnerabilities for a particular system. For example, knowing that the target mostly uses Niagara Fox, we won’t spend much on finding new exploits for Codesys products;
- Ports — other open ports on a device might provide an entry point for attackers. Obsolete and vulnerable Apache servers can be used to get deeper into the network;
- Response from a device — it provides a lot of useful and detailed data about the running device. It’s also super helpful in order to establish a real location of the building in which the device operates. During installation, technicians often put the name of the street, building, exact location, phone number or other sensitive information in the description.
Example fields from BACnet devices:
- Vendor ID
- Vendor Number
- Object Identifier
- Firmware Revision
- Application Software Revision
- Object Name
- Model Name
- Description
- Location
- Broadcast Distribution Table (BDT)
- Foreign Device Table (FDT)
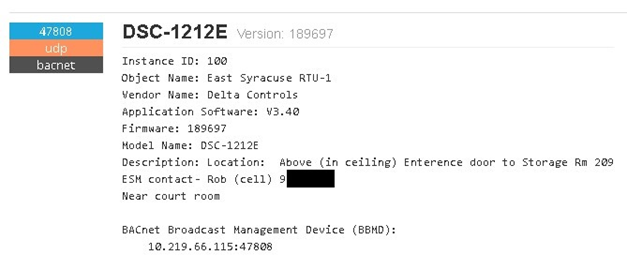
Example response from a BACnet device exposing phone number and location
Example fields for Niagara Fox:
- Fox Version
- Hostname
- Host Address
- Application Name
- Application Version
- Station Name
- VM Name
- VM Version
- OS Name
- Time Zone
- Host ID
- VM UUID
- Brand ID
Example of real raw response from a Niagara Fox device:
fox a 0 -1 fox hello\n{\nfox.version=s:1.0.1\nid=i:255149\nhostName=s:192.168.1.11\nhostAddress=s:192.168.1.11\napp.name=s:Station\napp.version=s:3.8.311\nvm.name=s:Java HotSpot(TM) Embedded Client VM\nvm.version=s:25.141-b06\nos.name=s:QNX\nos.version=s:6.5.0\nstation.name=s:Guadelupe_Jail\nlang=s:en\ntimeZone=s:America/Chicago;-21600000;3600000;02:00:00.000,wall,march,8,on or after,sunday,undefined;02:00:00.000,wall,november,1,on or after,sunday,undefined\nhostId=s:Qnx-JVLN-0000–05A1–7B93\nvmUuid=s:11e98b97-b656–1c50–0000–00000000bafd\nbrandId=s:vykon\nsysInfo=o:bog 61[<bog version=”1.0″>\n<p m=”b=baja” t=”b:Facets” v=””/>\n</bog>\n]\nauthAgentTypeSpecs=s:fox:FoxUsernamePasswordAuthAgent\n};;\nfox a 1 -1 fox rejected\n{\n};;\n

Photo by Jannes Glas on Unsplash
Collecting data
As stated before, this research is based only on data gathered in a passive way. There are two services I used, Shodan and BinaryEdge, and both of them allow users to search the Internet for connected devices, including ICS. Thanks to additional filters, you can find what interests you or narrow your search to a specific country, product or version.
In contrast to Shodan, BinaryEdge provides ready-to-use queries to filter all possible ICS devices, but does not support geolocations. To use this solution, one needs to have their own IP geolocation database and use it against collected IP addresses. Free databases are not very accurate, but the best one available is Maxmind. Shodan, on the other hand, gives geolocation data for the device directly from the API and no further checks have to be applied. However, to use tags and list every ICS device (like BinaryEdge does) one needs to have “enterprise” access, which is expensive.
The list of searched devices is the same as in the previous research:
-
- Modbus
- Siemens S7
- Tridium
- General Electric
- BACnet
- HART IP
- Omron
- Mitsubishi Electric
- DNP3
- EtherNet/IP
- PCWorx
- Red Lion
- Codesys
- IEC 60870–5–104
- ProConOS
To actively look for exposed devices in the US, one needs to scan 1,573,564,566 IP addresses, categorize them, geolocate, and put them on a map. It’s not impossible knowing the default ports of ICS devices and the response they return. To achieve this, it’s best to use masscan, or a similar tool, with regular expressions matching response. The full list of nmap regex can be found here: https://svn.nmap.org/nmap/nmap-service-probes.
Regular expression for detection of a Niagara Fox device:
match niagara-fox m|^fox a 0 -1 fox hello\n\{\nfox\.version=s:([\d.]+)\nid=i:\d+.*\napp\.name=s:Station\napp\.version=s:([\d.]+)\n|s p/Tridium Niagara/ v/$2/ i/fox version $1/ cpe:/a:tridium:niagara:$2/
Regular expression for detection of an Allen-Bradley management server:
match http m|^HTTP/1\.0 200 OK \r\nServer: A-B WWW/([\d.]+)\r\n.*<img src=\”/images/rockcolor\.gif|s p/Allen-Bradley WWW httpd/ v/$1/ i/Rockwell Automation Ethernet Processor http config/
In addition, to get more details, Nmap Scripting Engine (NSE) scripts are needed. They send the proper payload in order to get a specification from device in return.
Active scanning is not stealthy and requires more effort than passive gathering, but in my opinion results would be very similar.
Kamerka
The first version of Kamerka allowed simple visualization of cameras for a given location. Based on this, it shows assets that might not be in a company’s netblock, but operate nearby or in the building owned by them, therefore belong to them. It could also be used for spying, by hacking cameras or finding ones without authentication. By creating this I wanted to highlight the issue of Internet-facing cameras near buildings with high military or commercial value.
Of course, the IoT world consist of more devices than just cameras, so the second version of Kamerka also covers printers, Message Query Telemetry Protocol (MQTT), and Real-Time Streaming Protocol (RTSP). All of these can be abused if not properly secured. Moreover, some of the protocols, like MQTT, are often used in critical infrastructure as smart sensors which process confidential measurement data from a facility.
Example of Industrial Internet of Things (IIoT) devices running in a New York power plant:
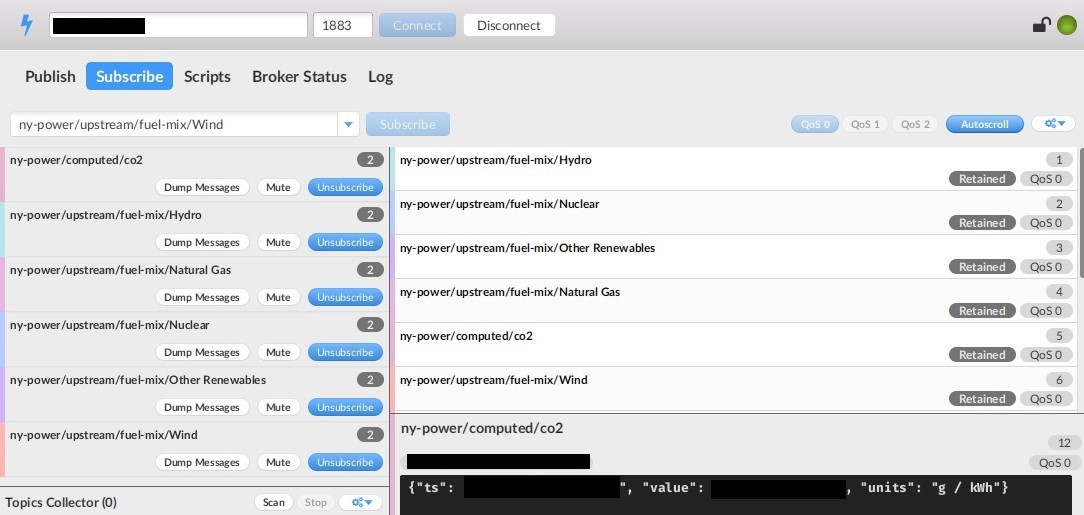
Industrial Internet of Things
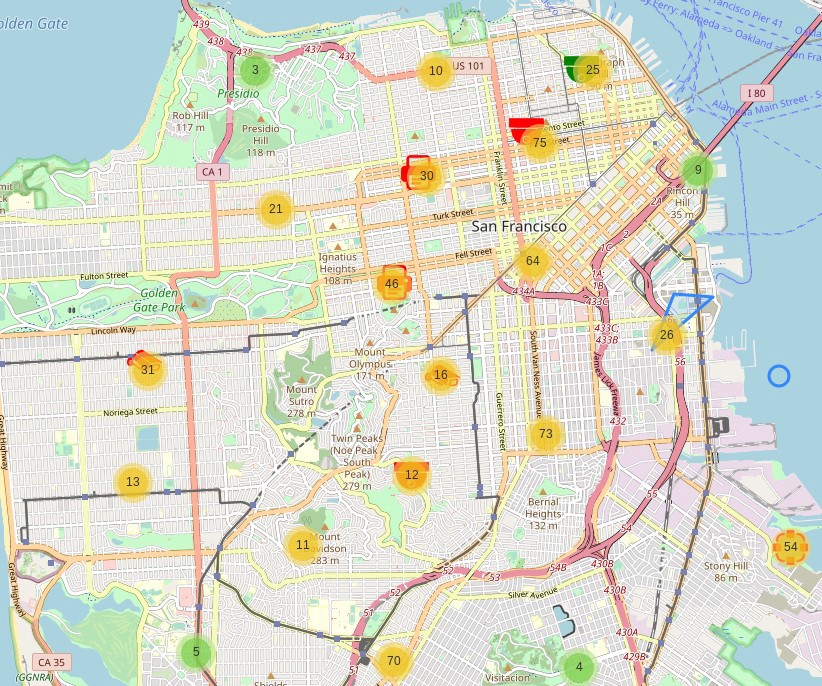
In the last version of Kamerka you can scan a country for ICS devices and put the results in a map with all the details, including who owns a specific IP address. Last time, Poland and Switzerland were shown as an example, but for this research I got 26k exposed devices in the US. I had to tweak the script a little to gather a larger amount of data than usual and put it in Elasticsearch for easier management. The map goes blurry with all devices displayed at once, but having the information stored, it’s possible to create different maps based on specific queries.
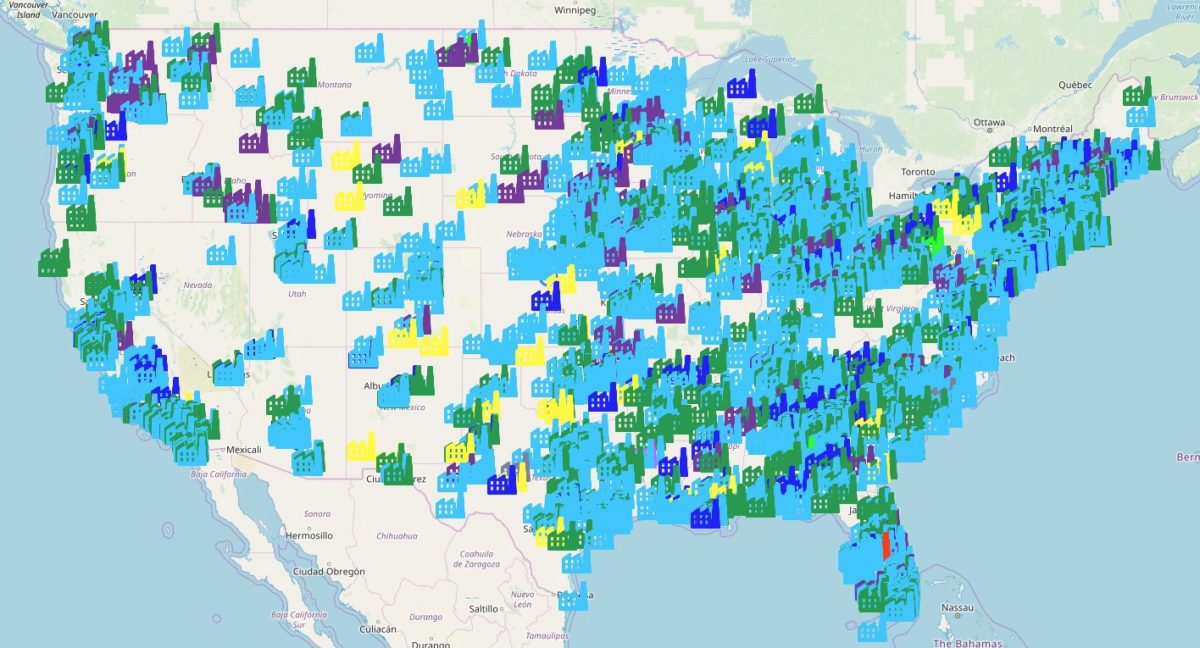
Map of 15k exposed devices in the US
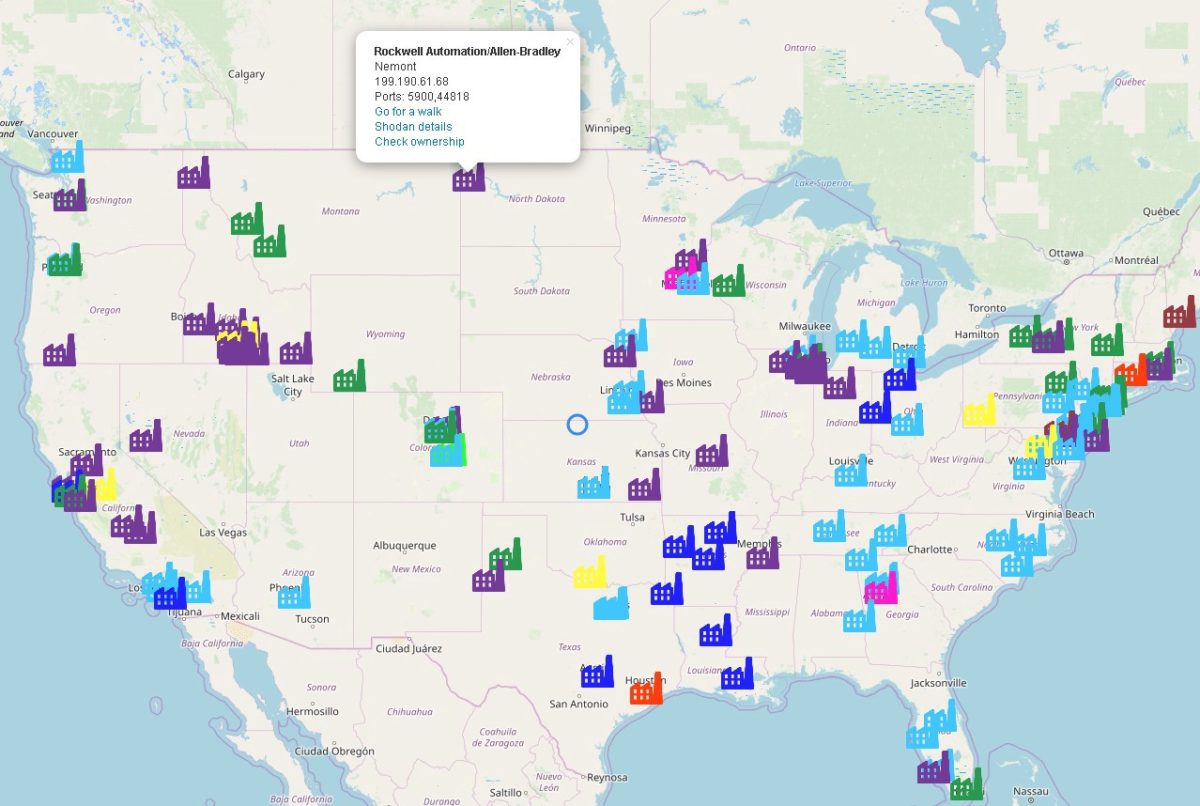
Devices with port 5900 (Virtual Network Computing) open:
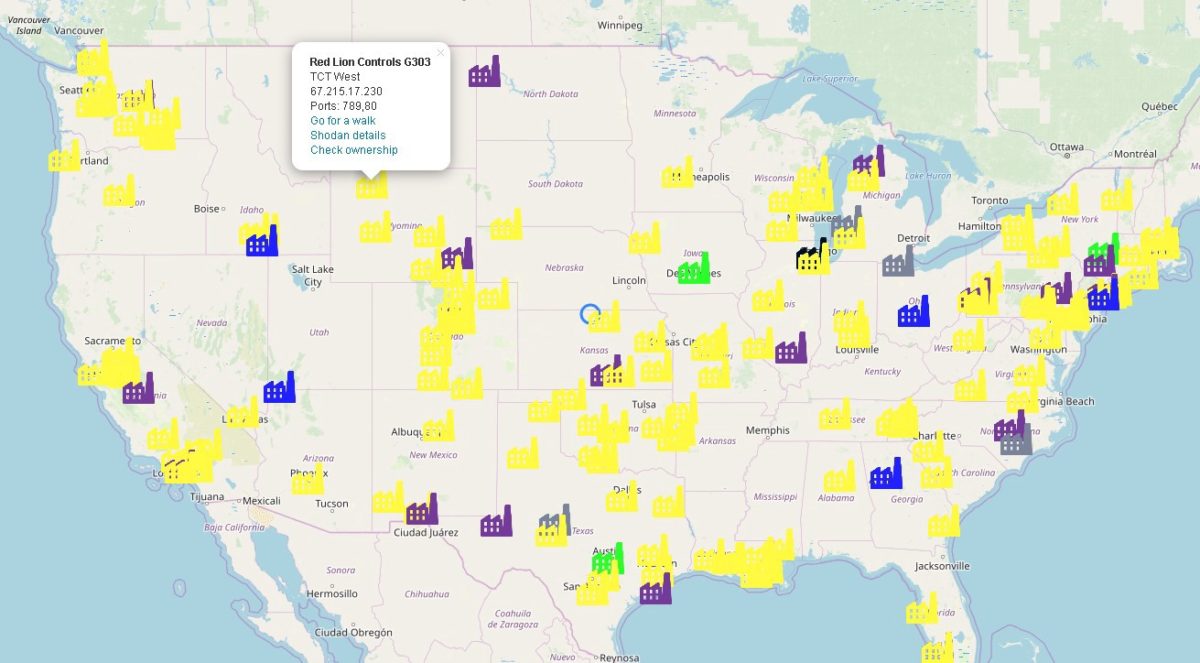
Devices with port 789 for Red Lion Controls open:
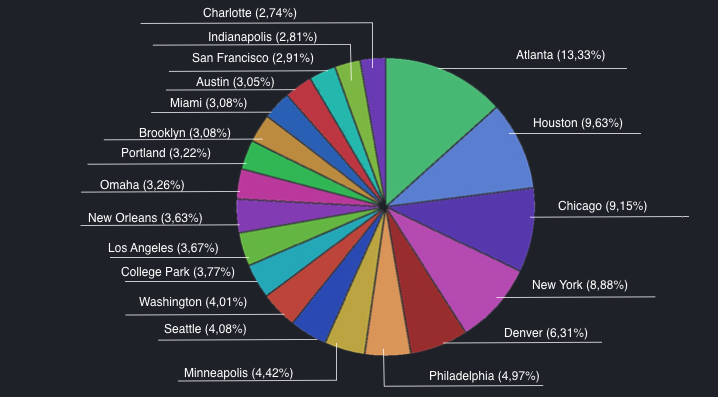
Statistics
Before we go to geolocation and identification, I will present some statistics.
Most affected organizations:

Most affected cities:
Open ports:
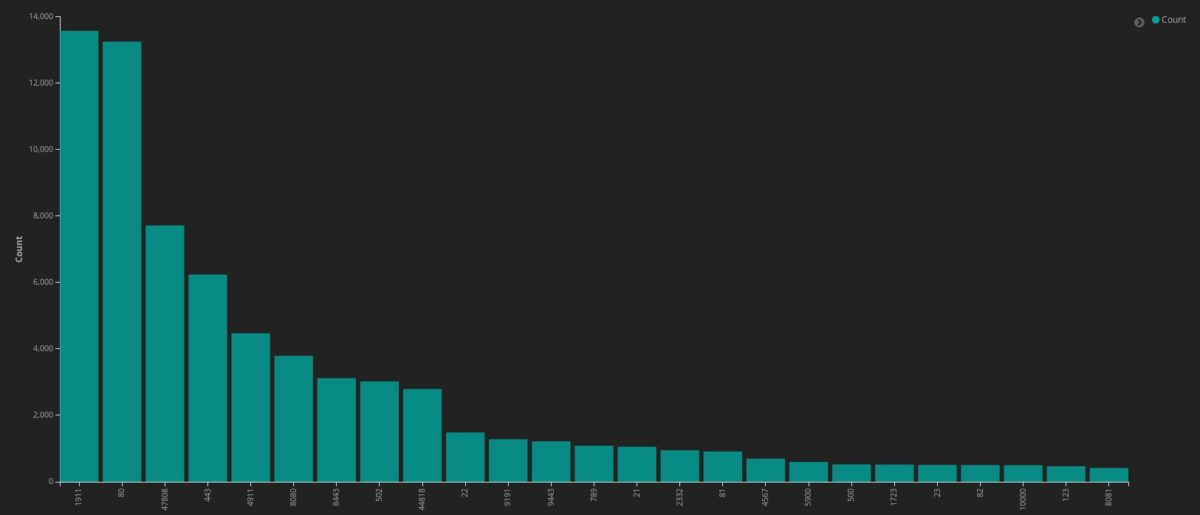
Top 5 ICS ports:
1911
47808
4911
502
44818
Top 5 other ports:
80
443
8080
8443
22
Findings
As seen above, a lot of devices have a management panel exposed on port 80, 443 or 8080. It’s convenient for remote technicians to manage devices without physically coming on site. However, from a security point of view, additional aspects should be applied to this solution. Default or weak passwords are the most common and irresponsible thing that might happen to a device, no matter if they are ICS or IoT devices.
OSINT is also about reading documentation and systems guides to gain information on how something works and what features can be used to get more information or full access.
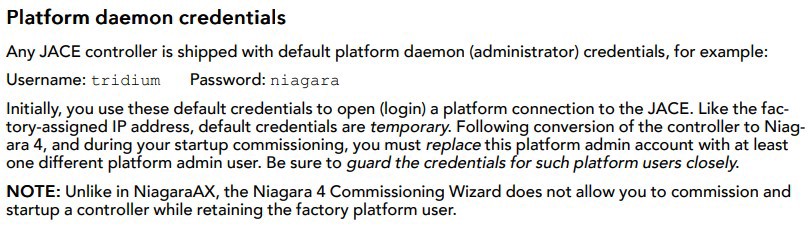
Manual for Niagara device
Full list of known default credentials has been published.
There are a lot of panels operating on unsecured port 80 or 8080.
Niagara Fox login panel
Niagara Fox login panel
Omron login panel
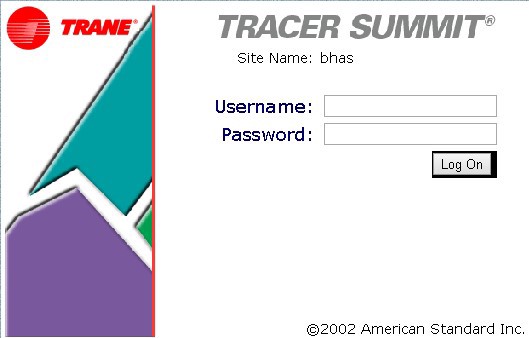
Tracer login panel
In addition, you can get another valuable hint from login panels. Some of them include, besides the name of the site, a picture of the organization or facility. Thanks to that, it’s possible to narrow results to a specified brand.

Some of the devices expose their network configuration, diagnostics info, statistics or settings without the need to be authenticated. That’s another indicator, which helps getting a full picture of running infrastructure.
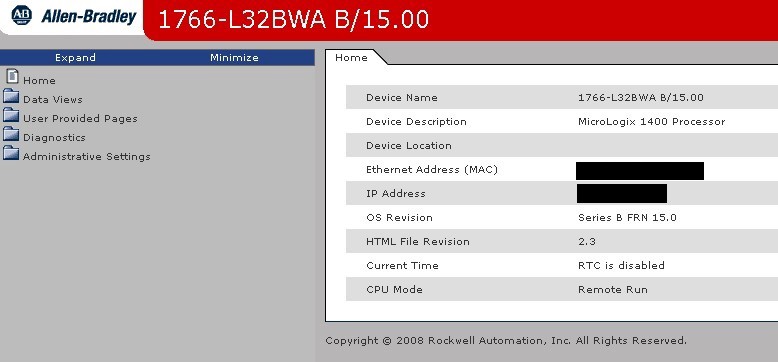
The information exposed could be useful if someone has established access to the network and looks for potential ICS devices. It includes IP address, subnet mask, gateway address or name servers. On many occasions I saw the use of an external DNS system, which opens doors for different kinds of attacks.
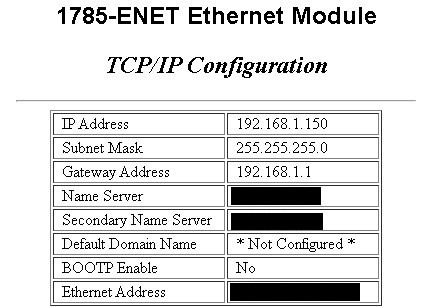
It’s not the best idea either to run VNC without authentication on ICS devices. It’s just something that should not happen at all and it’s a clear mistake or lack of knowledge of your own infrastructure. From an adversary’s perspective it’s an easy win — he can get access without authentication and gain control over the device. Of course, we won’t call it compromising the entire facility but it’s a good start for sure. All VNC operates as a Human-Machine Interface (HMI) on port 5900.
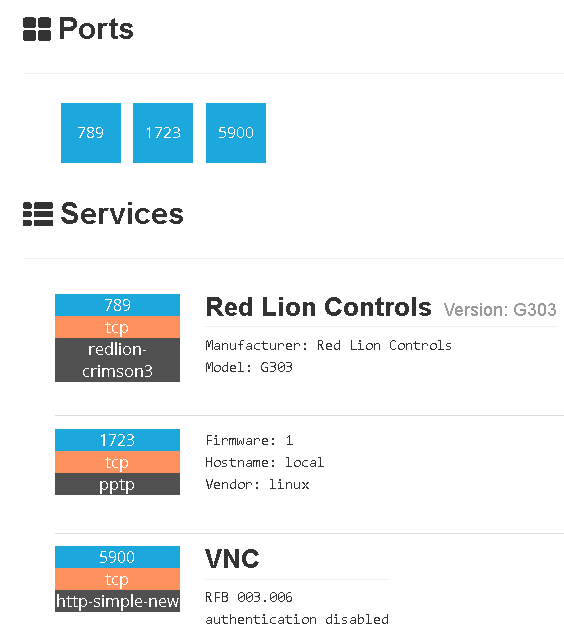
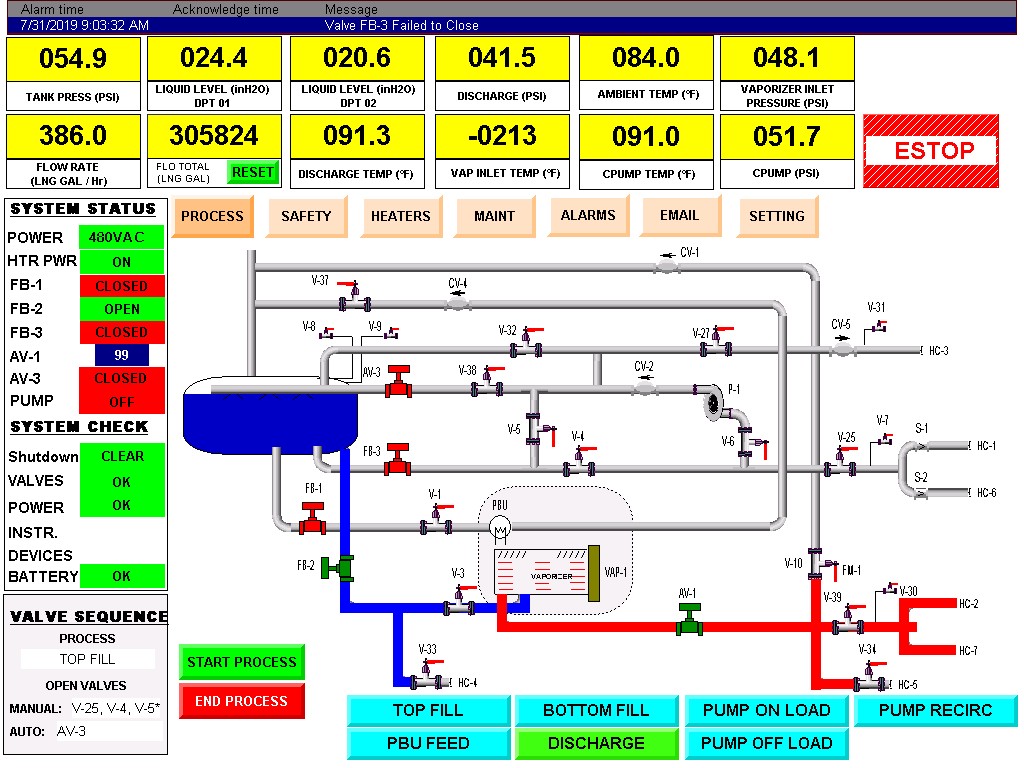
VNC is not the only way devices could be exposed; port 80 on devices from specific manufacturers return an HMI without authentication. Some of the websites require logging in for interaction but it’s not always necessary.
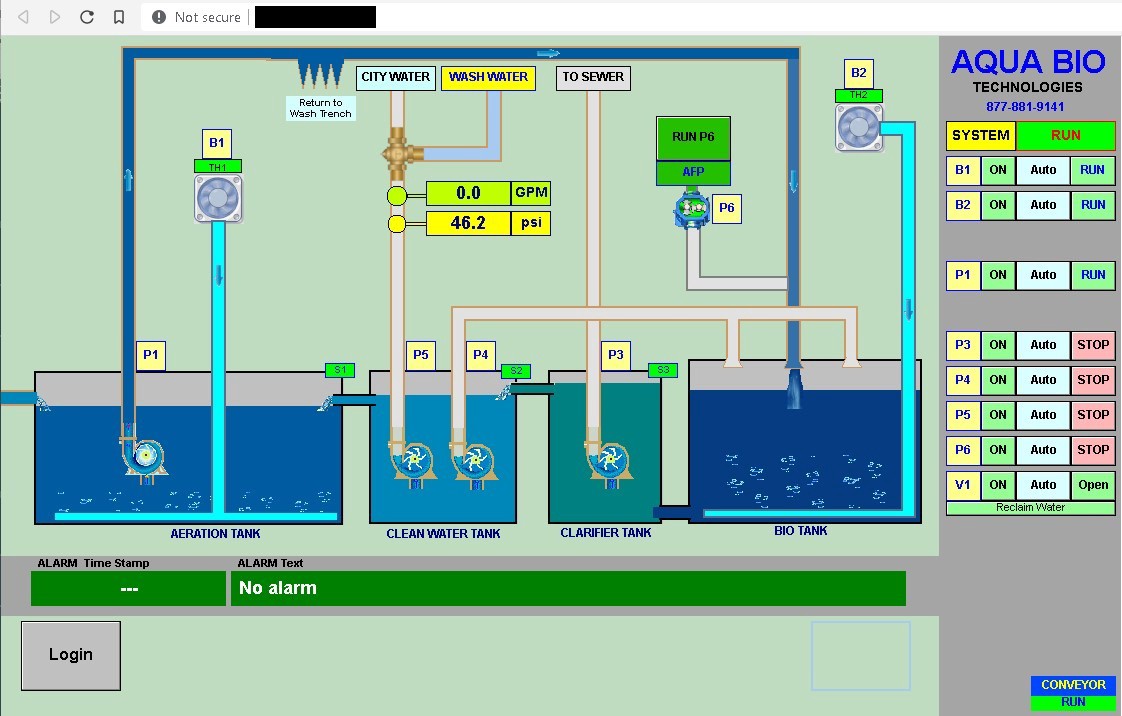
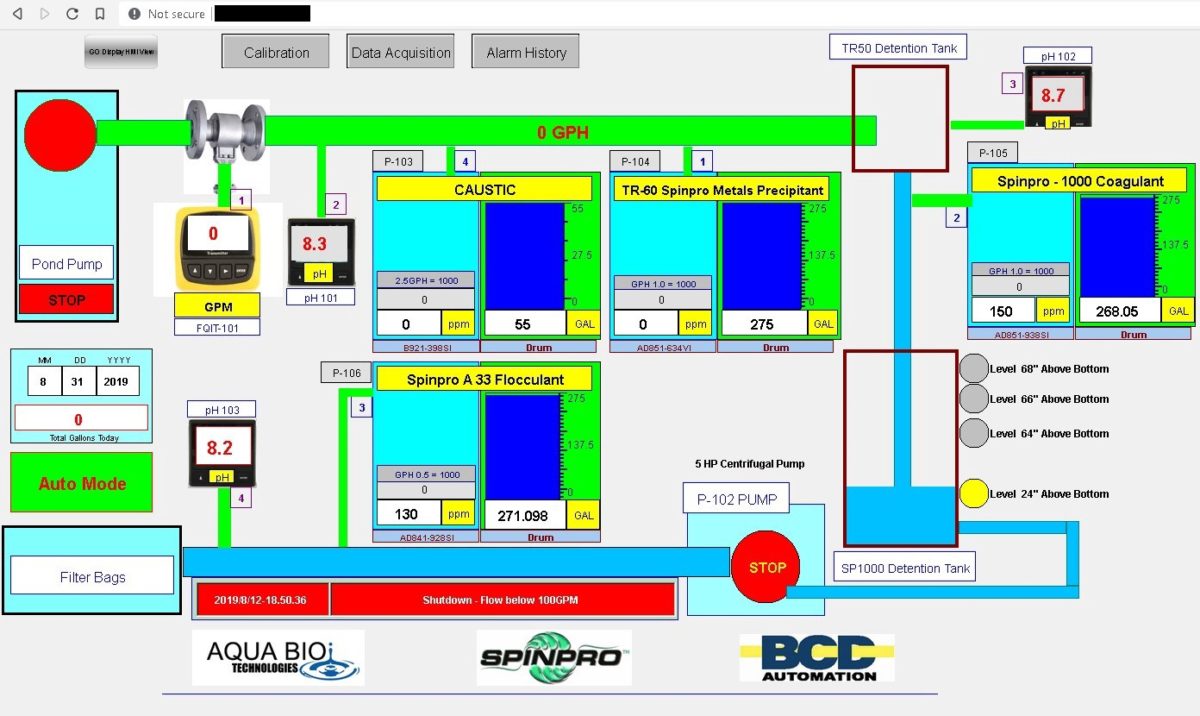
As you may notice, there is another indicator for determining connections and geolocating a building or facility. The HMI itself reveals use of the device so it’s easy to recognize if it’s a car wash or a device in a wastewater plant. Technology and brands displayed on the screen also tell us much about specifications and how a device might be used.
Geolocation
To target only critical infrastructure one needs to exclude devices with no strategic meaning. For example, devices that manage a fountain in the park, which might be exposed but there is no profit from compromising it and for sure it’s not critical infrastructure to anyone.
So how to find devices and buildings responsible for critical infrastructure? You can use the generated map and check each device nearby places of interest, like cities or government buildings. The second method involves running a reverse search and looking for artifacts from devices, i.e. station name, description or location. As mentioned before, Niagara Fox and BACnet sometimes reveal more data than they should, including street name, location or name of the facility. Merging it with other indicators can allow you to find the proper building. IP geolocation is not always precise — it does not point to the exact place but it can accurately show the city and sometimes it can show the street where the device may be located.
To prove my words, I will present a few cases where the information I gathered allowed me to find a building with strategic meaning to the country or a city.
Water and Wastewater Systems sector
You already know what kind of sectors should be protected with special care and one of them is the water and wastewater systems sector. When disrupted, drinking water could no longer be available, causing problems for businesses and society.
In this case, the name of the facility is disclosed in the “station.name” field of the Niagara Fox device.
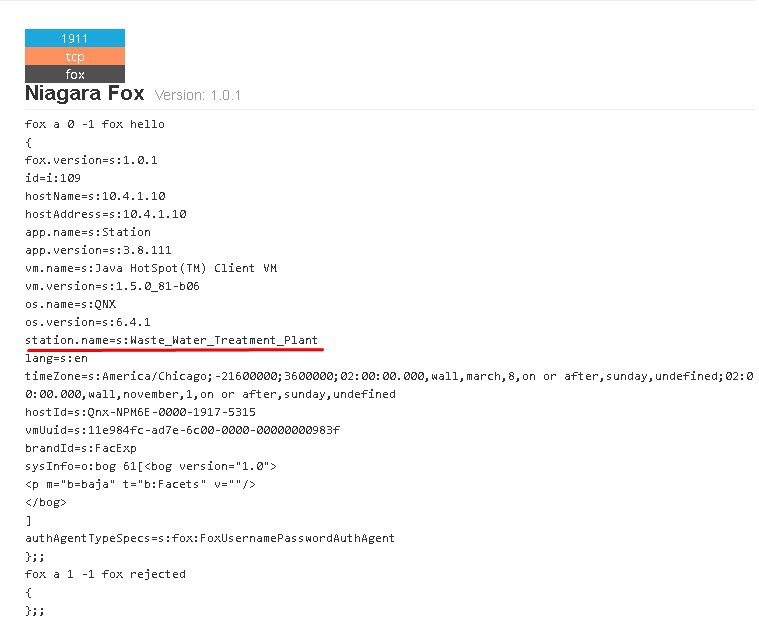
IP geolocation points to 14 Summer Street in Burlington, Vermont, which is 1.5 miles from the nearest wastewater plant.
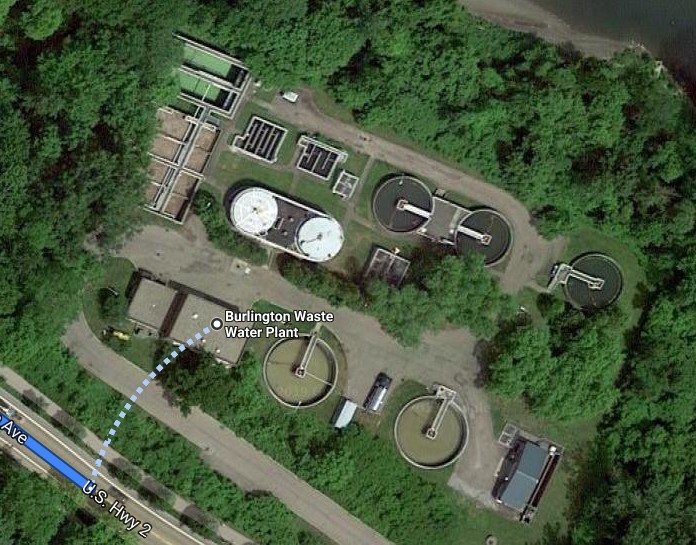
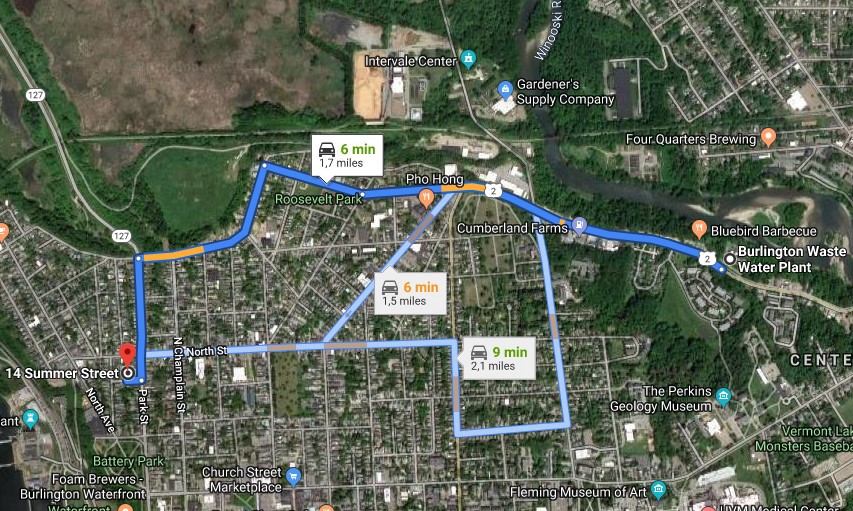
Having this information, the next step would be to prepare physical surveillance and active intelligence gathering by scanning the asset and looking for more on the network.
Chemical sector
When you manage a lot of stations, you have to know what you are connected to. This example shows that comfort is the enemy of security. The location of the site is exposed in the device and even without proper geolocation it’s possible to obtain the location of the building.
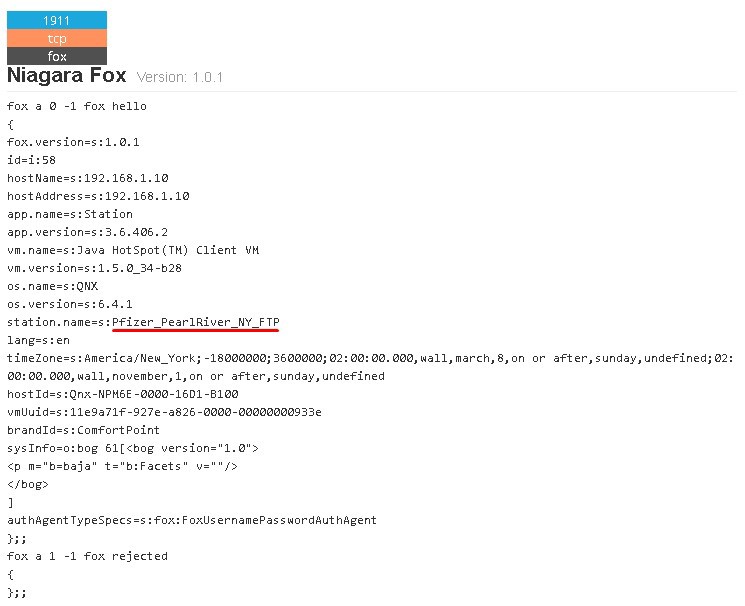
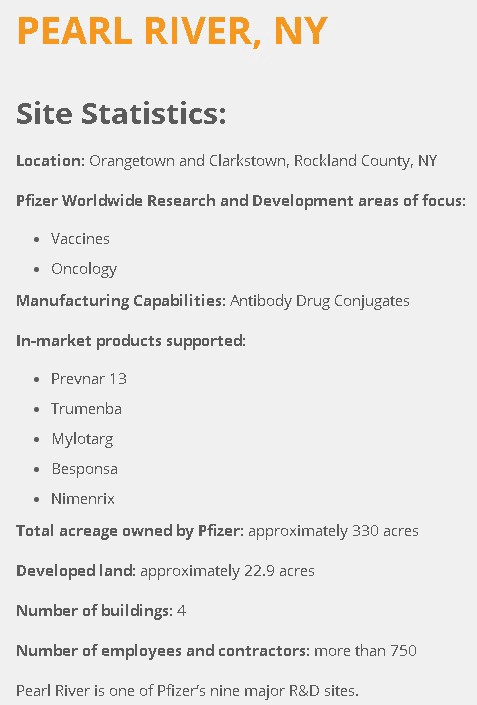
“Station name” contains information about the place (Pearl River), state (New York) and organization name (Pfizer).
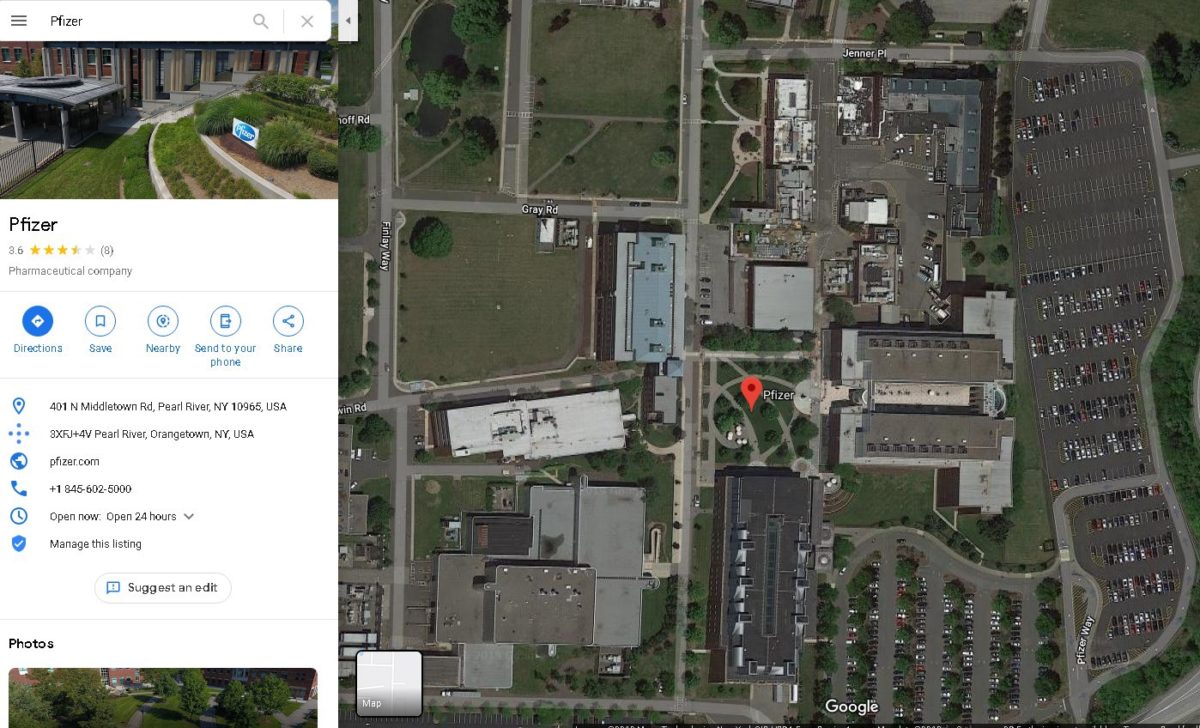
From their official website, we can learn that it’s one of the nine major Research and Development sites of Pfizer.

Healthcare sector
Devices in every hospital are very fragile and disruption of services can lead to rescheduled patient operations or can cause irreparable health problems, including death. These facilities should have special security controls implemented and should not allow remote connections. One of the examples of misconfiguration for the healthcare sector is Piedmont Hospital. In this case, the exact location is exposed — street, city and state.
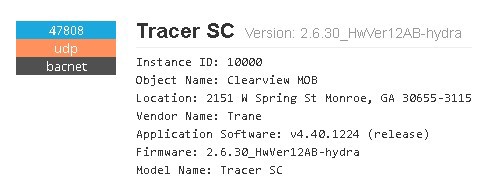
This is also a good example for testing geolocation capabilities — knowing the precise location of the device, we can see if IP geolocation is accurate.
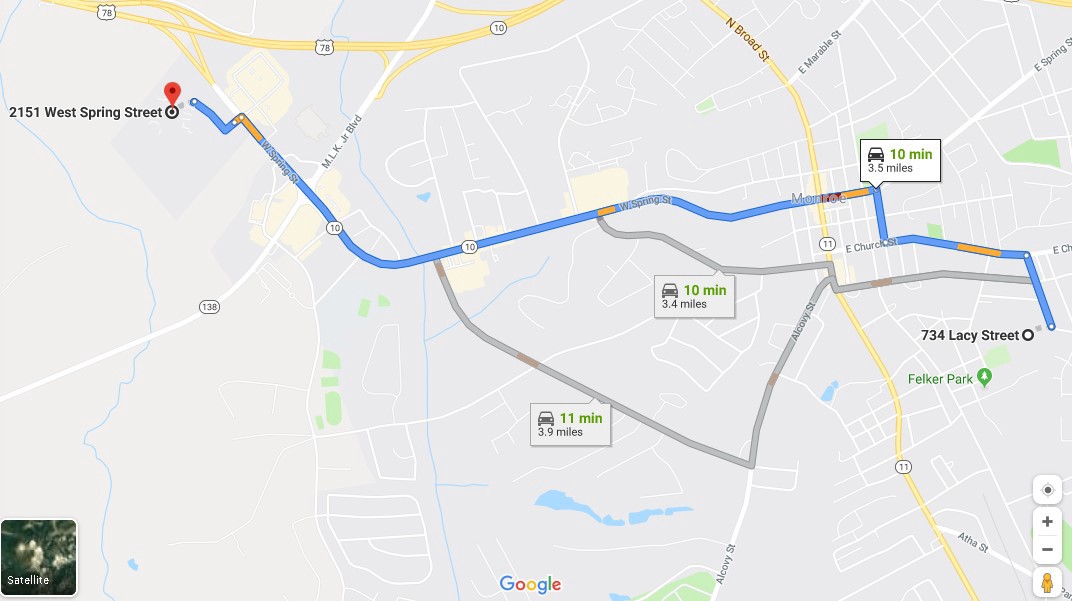
In this case it’s 3.5 miles away from the target — 2151 West Spring Street.
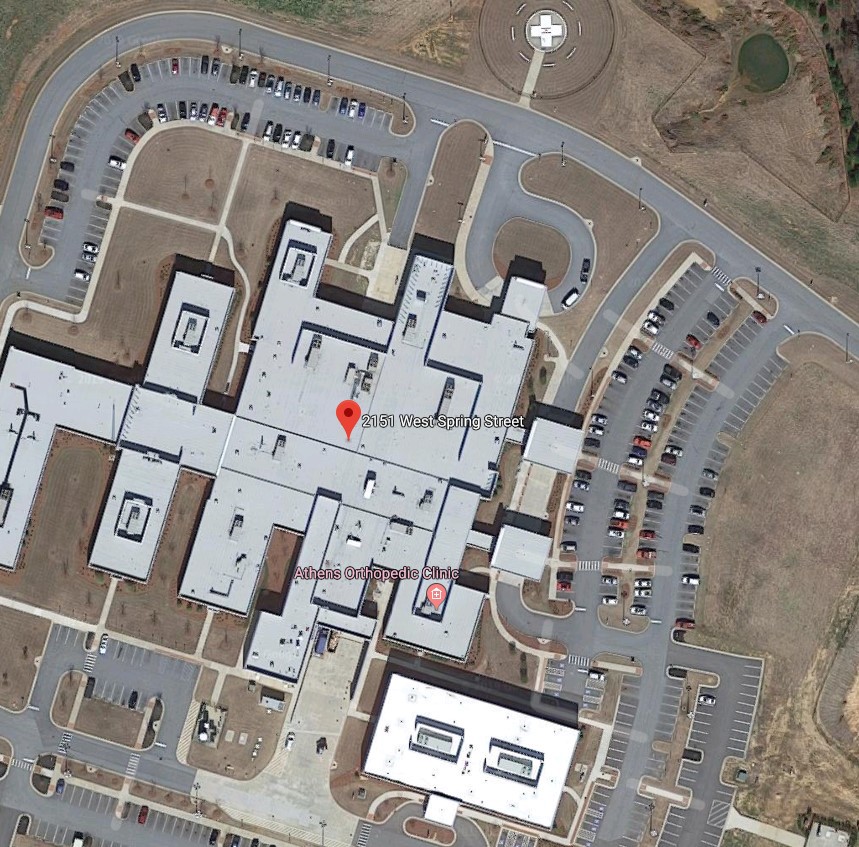
In some cases, you can get an inside view of the building from official sites. Every floor and room is covered, including conference rooms, storage and plant operations. It’s another indicator that shows it’s possible to gain precise intelligence. You can see how valuable it would be to have insider knowledge of the facility. Someone could be able to connect to the device and wreak havoc, but of course it also depends on what the device is actually used for.
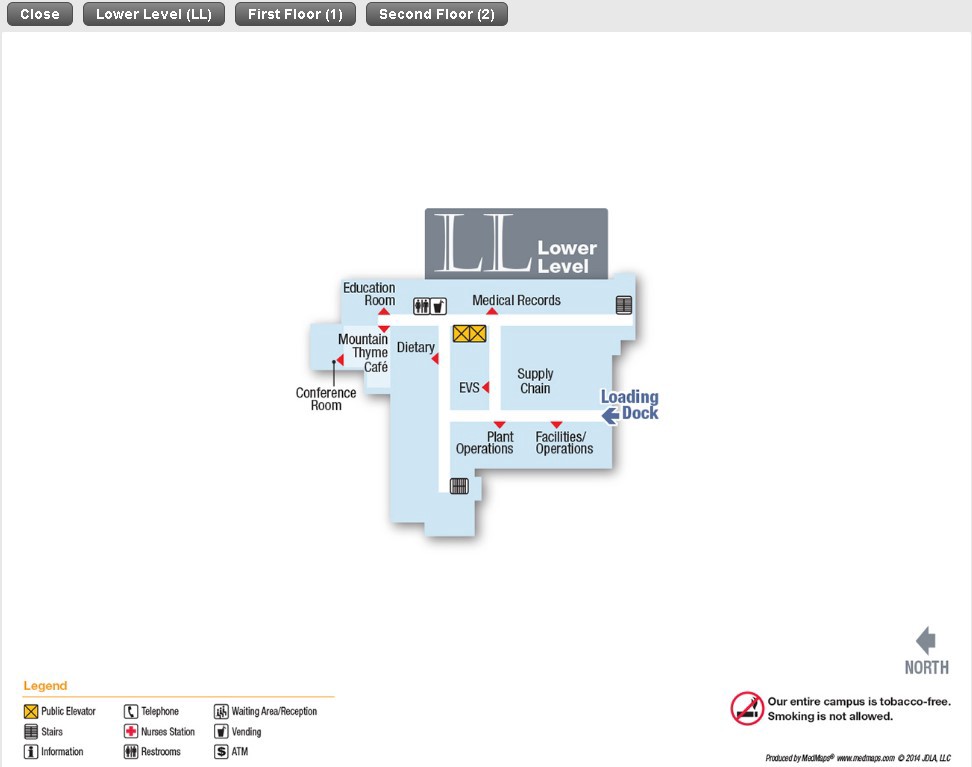
Energy sector
The energy sector is very specific because of the high dependencies to other sectors, like manufacturing or government facilities. Without a stable energy supply, societies and businesses can’t function properly. Based on previous cyber attacks, it’s one of the most targeted sectors — we could see the attacks on Ukraine’s power grid that caused outages for a few hours and could paralyze whole cities.
It happens sometimes that IP geolocation can’t be defined — it just points to the center of the country. If there are no additional indicators, it’s impossible to find the location.
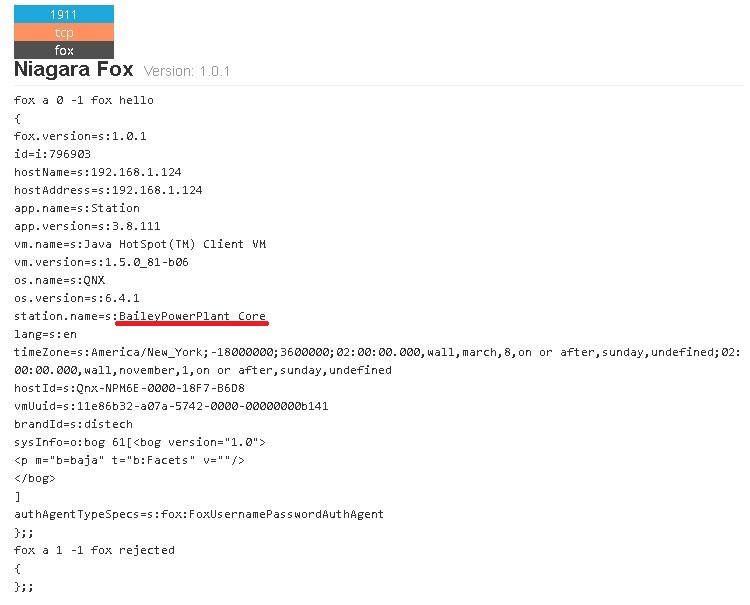
“Station name” clearly provides the name of the facility and probably the function of the device, “Core”.
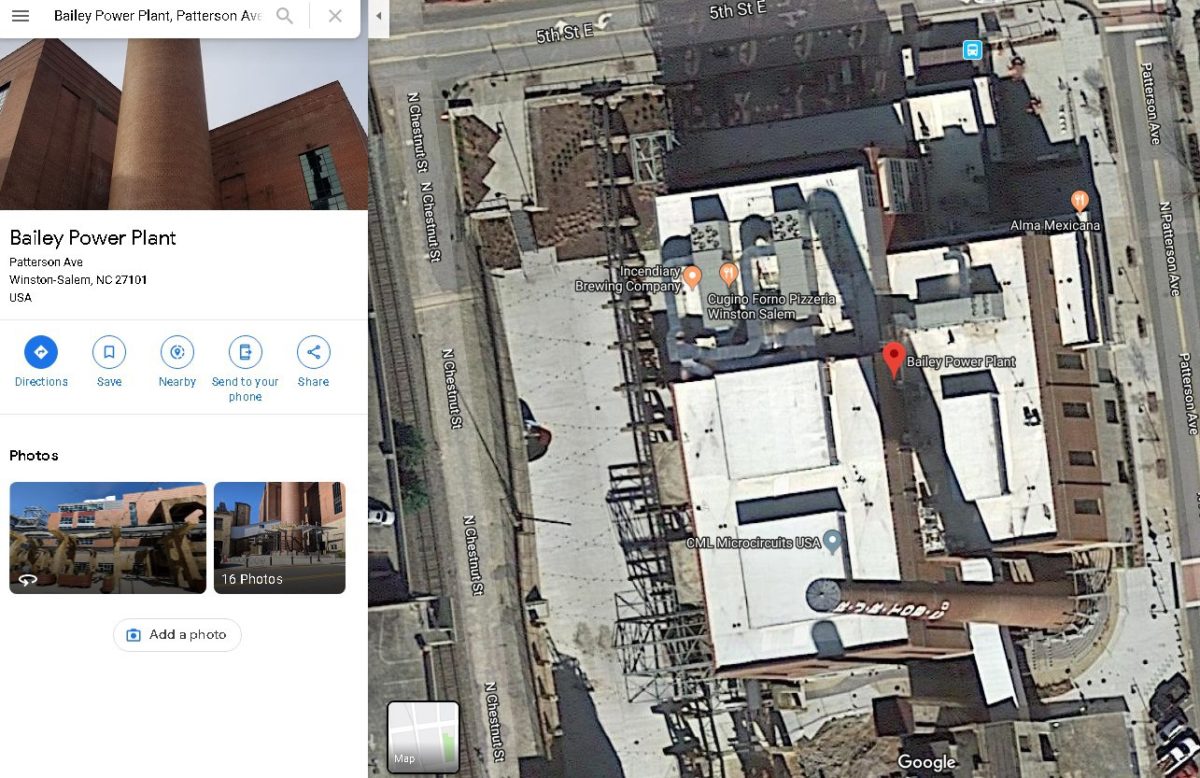
There is a famous power plant in Winston-Salem that has been renovated recently and hosts many events.

Manufacturing/Defense Industrial Base sector
There are a lot of government contractors that work with classified materials, manufacture equipment or cooperate in other ways that could result in a threat to national security if their systems were to be exposed.
When geolocation has been defined, it’s enough to have the name of the company to find a facility.
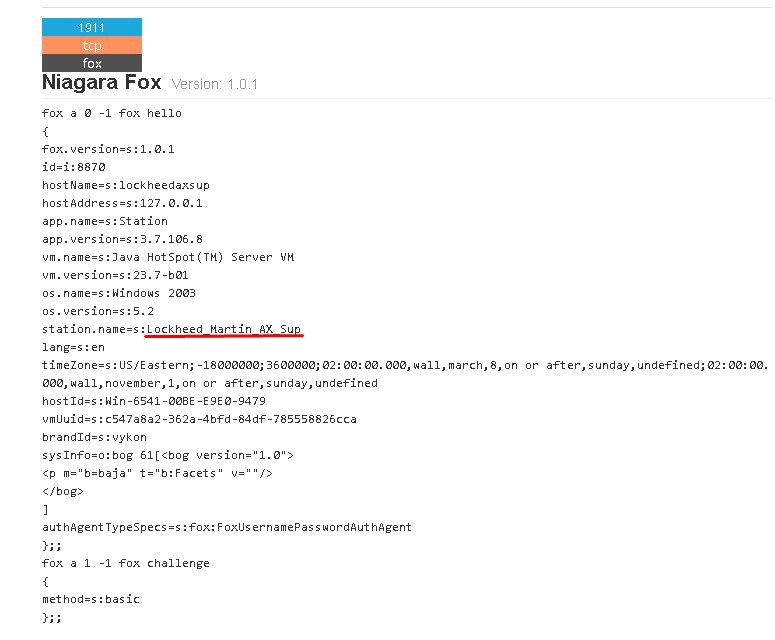
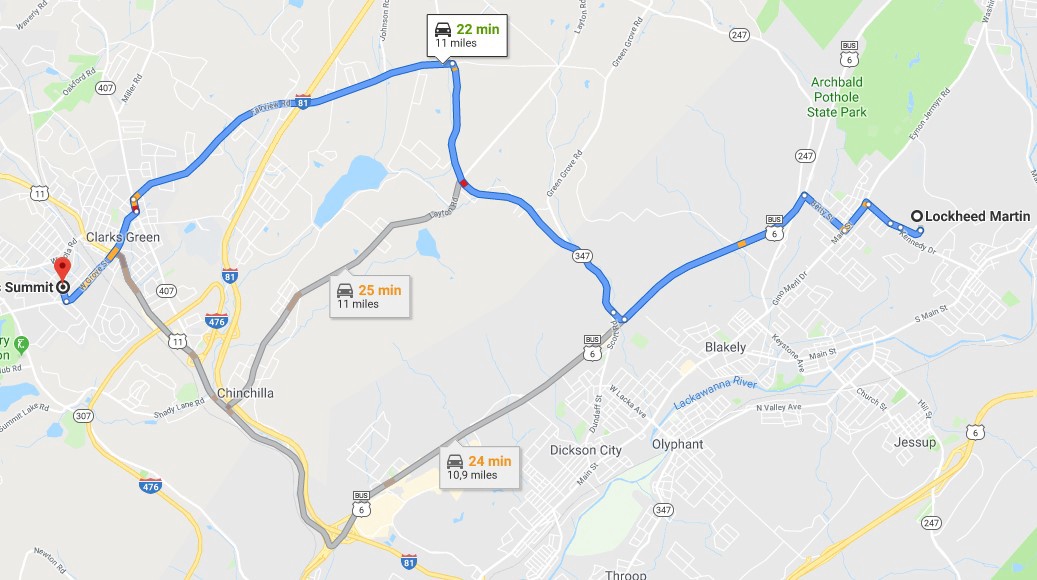
Geolocation points to Clarks Summit, Pennsylvania. The closest Lockheed Martin facility is 11 miles away.

From their official site we can get information about this specific facility and its role.
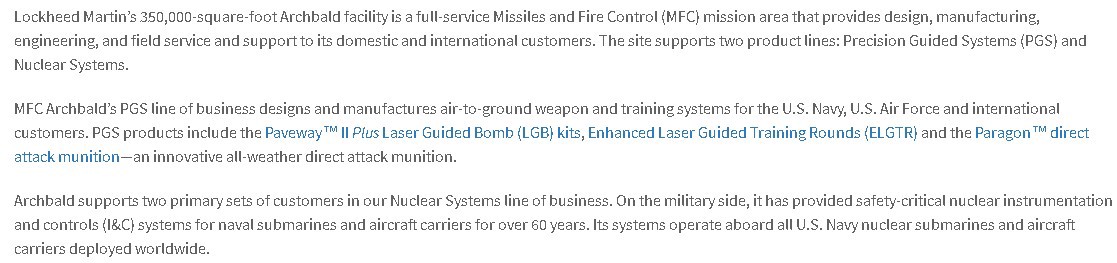
To compare the findings from Google Maps with a real view, we can go to the official Lockheed Martin website and find the building.

For the record, I reported the aforementioned findings to the adequate organizations, but got no reply at all.
Summary
Maintaining critical infrastructure and ICS devices is not an easy task even for experienced network engineers and mistakes happen all the time. When infrastructure is built without security in mind, you expose it to cyber attacks and espionage, especially when you operate in any of the critical sectors. Any cyber attack on the facility might cause outrages, money loss for companies or even get people killed, and it’s important to keep in mind that these sectors depend on each other and are necessary for everyone’s daily lives.
I differentiate four reasons why there are so many ICS devices exposed to the internet:
- Some of them are honeypots to track threat actors — Researchers set up traps imitating ICS infrastructure to see who is going after these types of devices and what are the tactics, techniques and procedures (TTPs) used during reconnaissance and attack. One of the examples of ICS/SCADA honeypots is Conpot;
- Comfort for technicians — companies engaged in the installation of ICS devices often allow for remote connections so that a technician doesn’t need to be called on site every time a configuration change is needed;
- Misconfiguration — mistakes happen to everyone and wrong firewall settings might be one of the culprits for a device being exposed. However, it’s important to track these mistakes and properly react in time;
- Money — it’s tied to a previous reason, comfort. Each technician visit would cost additional money if they need to physically visit the facility. Organizations want to save as much money as they can on everything, and often it’s security.
- Unfortunately, you cannot predict everything, but you can act proactively to fight against any type of misconfiguration that might reveal information about a facility or devices. Of course, when a device is exposed to the Internet, it’s open to different types of attacks, from script kiddies to experienced nation-state actors.
But there are some methods that can help you keep your infrastructure in order:
- Implementing an information classification program — what details can be used by threat actors for espionage or reconnaissance? This data should have restricted access and not be publicly available;
- Maintaining a detailed inventory — keep records of changes in your environment and try to understand potential external attack vectors;
- Active monitoring — monitor perimeter network security devices and utilize active reconnaissance techniques, like port scanning;
- Use free and open source tools — use tools such as BinaryEdge.io or Shodan to detect exposed devices that might belong to you. Focus on location and ICS-specific ports;
- Use open source intelligence gathering — gather as much information as an attacker would use to attack your infrastructure. Geolocation data, device details or personal data are valuable for threat actors. Try to understand what could be used against you in any way to compromise the facility.
Conclusion
I presented only 5 examples out of 26,000 devices that could be part of critical infrastructure. These facilities provide equipment or services that ensure the continuity of a country and play an important role for society. In the case of commercial industries, it’s their own role to secure their networks but if it’s about critical infrastructure it’s in the public’s interest to keep it safe.
Special focus should be applied by utilizing intelligence gathering methods on your own country’s critical infrastructure to know what information can be collected by threat actors. Additionally, the presented method allows you to gain data on adversary cyber potential and capabilities, as well as the strategic position of critical infrastructure.
References & further reading
https://www.cia.gov/news-information/featured-story-archive/2010-featured-story-archive/open-source-intelligence.html
https://www.dhs.gov/cisa/critical-infrastructure-sectors
https://www.boozallen.com/content/dam/boozallen/documents/2016/09/ukraine-report-when-the-lights-went-out.pdf.
https://dragos.com/wp-content/uploads/CrashOverride-01.pdf
https://ics.sans.org/media/E-ISAC_SANS_Ukraine_DUC_5.pdf
*This blog post has been edited by SecurityWeek for clarity
Register for the 2019 ICS Cyber Security Conference
Wojciech is a security researcher specializing in Open Source Intelligence. He has a background in pentesting and threat hunting, and his research covers Internet of Things, dark net and breaches, hence helping organizations all over the world. During his professional career as a cyber security expert, Wojciech provided analysis for companies across Europe. Moreover, he has delivered many open source tools to support the Open Source Intelligence community.
Intelligence Gathering on U.S. Critical Infrastructure
How Open Source Intelligence can be applied to reconnaissance on critical infrastructure. In many cases it’s possible to narrow a search to specific buildings like power plants, wastewater plants, or chemical and manufactured facilities. The research consists of 26,000 exposed devices in United States.