ICS Devices Vulnerable to Side-Channel Attacks: Researcher Shows
(Eduard Kovacs – SecurityWeek) Side-channel attacks can pose a serious threat to industrial control systems (ICS), a researcher warned last month at SecurityWeek’s ICS Cyber Security Conference in Atlanta, GA.
Demos Andreou, a lead engineer at power management company Eaton, has conducted an analysis of protection devices typically used in the energy sector, specifically in power distribution stations.
Side-channel attacks can be used to extract data from a system based on information gained by observing its physical implementation. There are several side-channel attack methods, but Andreou’s research looked at timing and power analysis attacks. These rely on the analysis of the time it takes to execute various computations, and the measurable changes in power consumption as the targeted device performs cryptographic operations, respectively.
The researcher says both timing and power analysis attacks can be launched against ICS devices. However, since timing attacks are easier to detect and block, he focused his research on power analysis.
While side-channel attacks have been known for a long time, few research papers describe their impact on industrial systems. It’s worth noting that the notorious Meltdown and Spectre side-channel attacks also affect ICS, but those methods involve only software and they rely on speculative execution, which helps speed up execution in modern CPUs.
Andreou told SecurityWeek in an interview that his goal is to raise awareness of the risks, show that attacks are not just theoretical, and that they could be conducted even with limited resources.
As part of his work at Eaton, Andreou conducts research into compliance and ethical penetration testing of industrial control systems and networks. Andreou and others help Eaton ensure that its products are secure and customer networks are not vulnerable to cyber threats.
Power analysis attacks rely on the power consumption changes of semiconductors during clock cycles, the amount of time between two pulses shown by an oscilloscope. The signals form a power profile, which can provide clues on how the data is being processed.
For example, a password can be obtained one character at a time by observing the power profile when a correct character has been entered compared to an incorrect character. An encryption key can also be extracted using the same technique.
Andreou said he conducted successful experiments on protection devices from three major vendors, but he believes products from other companies are affected as well if the microprocessors they use are vulnerable to these types of attacks.
While the tested devices are 5-10 years old, the researcher says newer products likely have the same vulnerabilities, as these types of attacks were until recently only theoretical and it’s unlikely that vendors took measures to mitigate the risks. The availability of open source software and inexpensive hardware have made it much easier to conduct side-channel attacks.
Andreou showed that an attacker who has physical access to protection devices can use an oscilloscope and a specialized hardware device running open source software to obtain an encryption key. The hardware required for such attacks costs roughly $300, the researcher said.
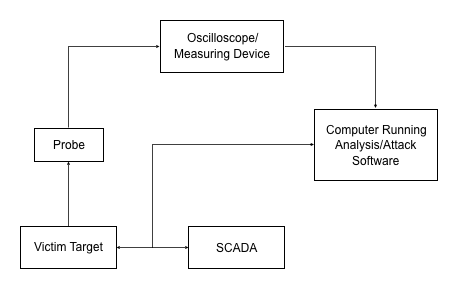
In the case of the analyzed protection devices, an attacker can extract the encryption key and use it to make configuration changes. Since these systems are used to protect the power grid, changing their settings can have serious consequences, Andreou told SecurityWeek.
A malicious actor could cause the system to fail or have it send false data back to its operator. These devices are distributed and they are controlled by a master system. Incorrect readings from one device can have repercussions for a different part of the network.
Furthermore, the researcher explained, an attacker could make configuration changes that are not immediately obvious. For instance, some of the analyzed protection devices have different settings for different seasons and a hacker could ensure that the changes they make would only go into effect when a certain season starts, which would disguise the attack.
Power analysis attacks can pose a serious threat because they are practically impossible to detect, as an attacked device could seemingly continue performing its normal operations even after it has been compromised, the researcher explained.
Conducting such attacks in a real-world scenario is not an easy task, but it’s not impossible. Andreou pointed out that it may not be difficult to obtain physical access to such devices as they are often left unsupervised. Malicious insiders, consultants, and repair centers could have plenty of opportunities to launch an attack.
On the other hand, the attack must be launched — i.e., the power consumption must be measured — exactly when the device performs an operation that involves the targeted crypto key. This requires reverse engineering the device and knowing ahead of time what type of product is targeted.
Conducting an attack could take hours, most of which involves physical preparation (e.g., opening the targeted device, connecting sensors). The software part of the attack is much faster and the key can be obtained in a matter of minutes.
For instance, if the Advanced Encryption Standard (AES) is used, the attacker can extract the key one byte at a time. In the case of AES-128, all they need to do is go through combinations from 00 to 255 for each of the 16 characters of the encryption key and monitor power profiles for each attempt.
Additional technical details on the attack are available in Andreou’s presentation at the ICS Cyber Security Conference:
Side Channel Attacks Against ICS Devices from SecurityWeek on Vimeo.
Related: Flaws Expose Siemens Protection Relays to DoS Attacks
Related: Risks to ICS Environments From Spectre and Meltdown Attacks
Side-Channel Attacks Put Critical Infrastructure at Risk
ICS Devices Vulnerable to Side-Channel Attacks: Researcher Shows (Eduard Kovacs - SecurityWeek) Side-channel attacks can pose a serious threat to industrial control systems (ICS), a researcher warned last month at SecurityWeek’s ICS Cyber Security Conference in Atlanta, GA. Demos Andreou, a lead engineer at power management company Eaton, has conducted an analysis of protection devices typically used in the energy sector, specifically in power distribution stations. Side-channel attacks can be used to extract data from a system based on information gained by observing
Rockwell Patches Vulnerability Impacting Safety Controllers From Several Vendors
(Eduard Kovacs - SecurityWeek) - In April, at SecurityWeek’s ICS Cyber Security Conference in Singapore, industrial cybersecurity firm Applied Risk disclosed the details of a serious denial-of-service (DoS) vulnerability affecting safety controllers from several major vendors. Rockwell Automation is one of those vendors and the company has now released patches for its products. In an advisory published last week, Rockwell Automation informed customers that the flaw impacts Allen-Bradley CompactLogix 5370 and Compact GuardLogix 5370 programmable automation controllers, which are used to control processes
Critical Vulnerabilities Found in Siemens Building Automation, Telecontrol Products
(Eduard Kovacs / SecurityWeek) - Industrial giant Siemens this week warned that critical vulnerabilities have been found in some of its telecontrol and building automation products, and revealed that some SIMATIC systems are affected by a high severity flaw. One advisory published by the company describes several critical and high severity flaws affecting Siveillance and Desigo building automation products. The security holes exist due to the use of a vulnerable version of a Gemalto license management system (LMS). The bugs affect Gemalto
Bechtel Opens Industrial Cyber Security Lab
Global engineering and construction giant Bechtel has opened a new cyber security lab aimed at protecting industrial equipment and software that control facilities such as power plants, chemical plants, and other large-scale critical infrastructure operations. With the goal of protecting industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems from cyber threats, Bechtel says the lab will leverage its experience designing and implementing National Institute of Standards and Technology Risk Management Framework (NIST-RMF) solutions for its government
Rockwell Automation Partners With Claroty on Industrial Network Security
Rockwell Automation is teaming up with industrial cybersecurity startup Claroty to combine their security products and services into future, combined security offerings. Rockwell, an industrial automation giant with more than 22,000 employees, said that after a competitive review process it selected Claroty for its anomaly-detection software purpose built for industrial network security. Armed with $32 million in funding through Series A and a Series B rounds, Claroty exited stealth mode in September 2016 to announce a security platform designed to provide “extreme
Exploring Risks of IT Network Breaches to Industrial Control Systems (ICS)
(SecurityWeek / Eduard Kovacs) - There have been several incidents recently where a critical infrastructure organization’s IT systems were breached or became infected with malware. SecurityWeek has reached out to several ICS security experts to find out if these types of attacks are an indicator of a weak security posture, which could lead to control systems also getting hacked. Security incidents involving critical infrastructure organizations There are only a few publicly known examples of cyberattacks targeting an organization’s industrial control systems (ICS), including
Kaspersky Launches Industrial Control Systems CERT
Kaspersky Lab has launched a new global computer emergency response team (CERT) focusing on industrial control systems (ICS). Through the Kaspersky Lab ICS-CERT, the security firm wants to share its knowledge and experience in securing industrial systems and coordinate the exchange of information between stakeholders. Officially launched last month, the new initiative aims to provide information on the latest threats, vulnerabilities, security incidents, mitigation strategies, incident response, compliance and investigations. Since it’s a non-commercial project, the Kaspersky Lab ICS-CERT will offer information and
Siemens Fixes Vulnerabilities in SIMATIC, License Manager Products
(SecurityWeek) - Siemens has released software updates to address several vulnerabilities in its SIMATIC and Automation License Manager (ALM) products. According to advisories published last week by both ICS-CERT and Siemens, the ALM, which allows customers to centrally manage licenses for their Siemens products, is affected by three vulnerabilities. The security holes, including one rated high severity and one rated critical, were reported to the vendor by researchers from Kaspersky Lab’s critical infrastructure team. The critical vulnerability, tracked as CVE-2016-8565, is a



