(Eduard Kovacs – SecurityWeek) – Kaspersky said it had detected roughly 18,000 malware samples belonging to more than 2,500 families on industrial control systems (ICS) in the first half of 2017.
According to the company’s “Threat Landscape for Industrial Automation Systems” report for the first six months of the year, nearly 38 percent of the industrial systems protected globally by its products were targeted during this period. This is 1.6 percent less than in the second half of 2016.
Attempts to download malware or access malicious websites (e.g. phishing pages) were blocked by the company’s products on over 20 percent of the protected ICS devices.
Windows malware was neutralized on more than half of targeted systems. However, in many cases, attackers used scripting languages such as VBS, JavaScript, .NET, AutoCAD, Word macros and Java to implement malicious functionality.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
“For computers that are part of industrial infrastructure, the Internet remains the main source of infection,” Kaspersky said in its report. “Contributing factors include interfaces between corporate and industrial networks, availability of limited Internet access from industrial networks, and connection of computers on industrial networks to the Internet via mobile phone operators’ networks (using mobile phones, USB modems and/or Wi-Fi routers with 3G/LTE support).”
The security firm, which last year launched a global computer emergency response team (CERT) focusing on ICS, noted that the number of attacks on these systems dropped in January, but returned to previous levels in the next months.
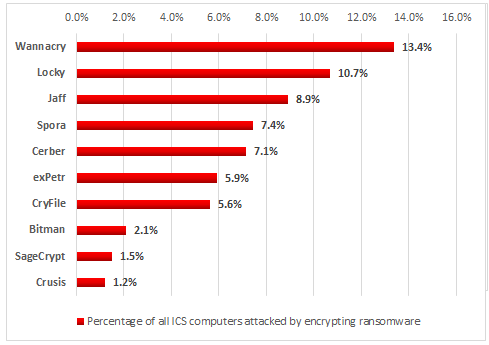
Kaspersky pointed out that many of the threats targeting ICS in the first half of 2017 were ransomware. The company’s products identified 33 different file-encrypting ransomware families on industrial automation systems.
Unsurprisingly, the highest percentage of attacks involved the notorious WannaCry ransomware, which leveraged NSA-linked exploits that can be triggered without user interaction.
Rockwell Automation, Schneider Electric, Honeywell, Siemens, ABB and other ICS providers published alerts at the time to warn customers about the possibility of being hit by WannaCry.
Thousands of Malware Variants Found on Industrial Systems: Report
(Eduard Kovacs - SecurityWeek) - Kaspersky said it had detected roughly 18,000 malware samples belonging to more than 2,500 families on industrial control systems (ICS) in the first half of 2017. According to the company’s “Threat Landscape for Industrial Automation Systems” report for the first six months of the year, nearly 38 percent of the industrial systems protected globally by its products were targeted during this period. This is 1.6 percent less than in the second half of 2016. Attempts to download
Iranian Hackers Target Industrial Firms
(Eduard Kovacs - SecurityWeek) - A cyber espionage group linked by security researchers to the Iranian government has been observed targeting aerospace and energy organizations in the United States, Saudi Arabia and South Korea. The threat actor, tracked by FireEye as APT33, is believed to have been around since at least 2013. Since mid-2016, the security firm has spotted attacks aimed by this group at the aviation sector, including military and commercial aviation, and energy companies with connections to petrochemical production. Specifically,
Siemens Partners With PAS on Industrial Cybersecurity
(Eduard Kovacs / SecurityWeek) - Engineering giant Siemens and PAS, a company that specializes in cyber security solutions for industrial control systems (ICS), announced on Tuesday a new strategic partnership. The goal of the partnership is to provide organizations the capabilities needed to identify and inventory assets, including distributed and legacy control systems, and provide visibility for detecting cyber threats and unauthorized engineering changes in multi-vendor environments. The solutions offered as a result of the partnership can be ideal for fleet-wide monitoring
Critical Infrastructure Attacks Drive Startup & Innovation Opportunities
By: Rick Grinnell, co-founder and managing partner of Glasswing Ventures. In this modern connected age, there’s no shortage of risks to fret about. I hate to add one more, but cyberattacks against utilities and power plants have recently rocketed to the top of the list of major security concerns. For instance, a June report from ESET released new research revealing that the Ukrainian power grid was taken down in late 2015 by the Win32/Industroyer malware. This malware has been considered the biggest threat to
Mocana Integrates Embedded Security Software With Industrial Cloud Platforms
Mocana Integrates Embedded Security Software with AWS IoT, Microsoft Azure IoT, and VMware Liota to Protect Devices (SecurityWeek / Kevin Townsend) - Two constants in current cybersecurity are the growing threat from insecure IoT botnets (Mirai, WireX, etcetera), and the continuing security provided by strong encryption. It is part of the mission of one venture capital funded firm to solve the former by use of the latter. Mocana was formed in 2002 as an embedded security software company for military applications. With the help
Russia-linked Hackers Target Control Systems in U.S. Energy Firms: Symantec
(Eduard Kovacs, SecurityWeek) - A group of cyberspies believed to be operating out of Russia has been observed targeting energy facilities in the United States and other countries, and the attackers appear to be increasingly interested in gaining access to the control systems housed by these organizations. The group, known as Dragonfly, Crouching Yeti and Energetic Bear, has been active since at least 2010, but its activities were first detailed by security firms in 2014. Many of the threat actor’s attacks have focused on



