Thousands of Malware Variants Found on Industrial Systems: Report
(Eduard Kovacs – SecurityWeek) – Kaspersky said it had detected roughly 18,000 malware samples belonging to more than 2,500 families on industrial control systems (ICS) in the first half of 2017.
According to the company’s “Threat Landscape for Industrial Automation Systems” report for the first six months of the year, nearly 38 percent of the industrial systems protected globally by its products were targeted during this period. This is 1.6 percent less than in the second half of 2016.
Attempts to download malware or access malicious websites (e.g. phishing pages) were blocked by the company’s products on over 20 percent of the protected ICS devices.
Windows malware was neutralized on more than half of targeted systems. However, in many cases, attackers used scripting languages such as VBS, JavaScript, .NET, AutoCAD, Word macros and Java to implement malicious functionality.
Related: Learn More at SecurityWeek’s 2017 ICS Cyber Security Conference
“For computers that are part of industrial infrastructure, the Internet remains the main source of infection,” Kaspersky said in its report. “Contributing factors include interfaces between corporate and industrial networks, availability of limited Internet access from industrial networks, and connection of computers on industrial networks to the Internet via mobile phone operators’ networks (using mobile phones, USB modems and/or Wi-Fi routers with 3G/LTE support).”
The security firm, which last year launched a global computer emergency response team (CERT) focusing on ICS, noted that the number of attacks on these systems dropped in January, but returned to previous levels in the next months.
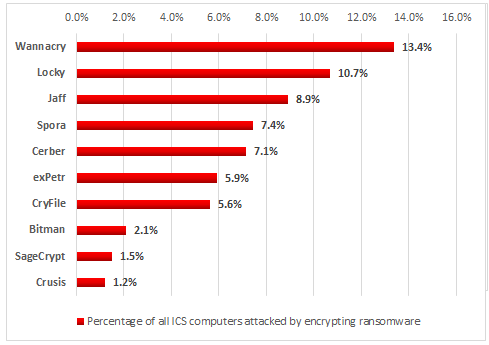
Kaspersky pointed out that many of the threats targeting ICS in the first half of 2017 were ransomware. The company’s products identified 33 different file-encrypting ransomware families on industrial automation systems.
Unsurprisingly, the highest percentage of attacks involved the notorious WannaCry ransomware, which leveraged NSA-linked exploits that can be triggered without user interaction.
Rockwell Automation, Schneider Electric, Honeywell, Siemens, ABB and other ICS providers published alerts at the time to warn customers about the possibility of being hit by WannaCry.
Add Comment
You must be logged in to post a comment.



